Access Restriction by Device/Browser
Access Restriction by Device/Browser in eCatalog
Enhanced Security Through Device and Browser Verification:
The Access Restriction by Device/Browser feature in eCatalog provides an additional layer of security by ensuring that users can only access the system from approved devices and browsers. This feature helps prevent unauthorized access from potentially compromised or unknown devices.
Key Functions of Device/Browser Access Restriction:
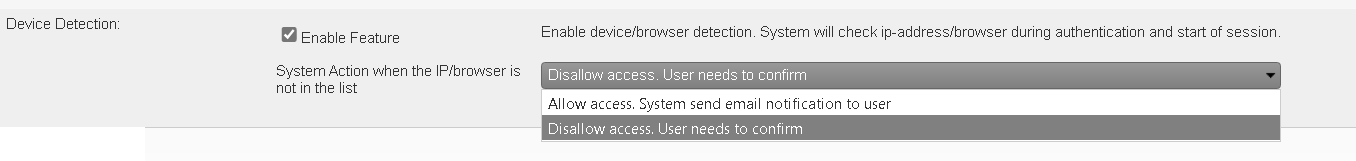
- Device/Browser Whitelisting:
- Initial Access: Upon their first login, the user’s device and browser are automatically registered and whitelisted in the system. This device becomes the approved point of access for that user.
- Subsequent Devices: If a user attempts to access the system from a different device or browser, the access can either be automatically denied or placed in a pending state until approval is granted, depending on the administrative settings.
- User Verification Process:
- Approval Required
Administrators can configure the system to require explicit approval for any new device or browser. In this scenario, the system sends an email to the user when a login attempt is made from a new device or browser. The user must approve this device by clicking a link in the email to enable access - Alert Only
Alternatively, the system can allow access from new devices or browsers but will alert the user via email about the new access. The user can then decide whether to continue allowing access from this new device or to block it.
Benefits of Device/Browser Access Restriction:
- Enhanced Security Controls
By limiting access to pre-approved devices and browsers, eCatalog can significantly reduce the risk of unauthorized access, providing an additional security measure against potential breaches. - User Empowerment
This feature empowers users to manage their own security settings by responding to alerts and approvals for device access, enhancing their control over personal security settings. - Adaptability and Flexibility
The flexibility to choose between automatic denial and user approval for new devices allows organizations to tailor their security approach to best fit their operational needs and risk profile.