Re-authentication Policy
Re-Authentication Policy in eCatalog
Enhancing Security with Targeted User Verification:
eCatalog incorporates a robust Re-Authentication Policy that allows administrators to specify which webpages or actions require users to undergo additional authentication. This feature is crucial for enhancing security, especially for actions or pages that are sensitive or pose a higher risk if accessed improperly.
Key Aspects of the Re-Authentication Policy:
Configurable Triggers:
- Selective Authentication:
Administrators have the flexibility to set up re-authentication prompts for particular webpages or actions, such as buttons or links. This means only specified elements will trigger the re-authentication process. - Re-Authentication Process:
- Popup Authentication
When a user attempts to access a protected page or perform a restricted action, a re-authentication popup will appear. Users must successfully verify their credentials to proceed. - Time-Limited Access
Upon successful re-authentication, the user will be granted access to the page or allowed to complete the action for a limited period, typically set to 60 minutes, ensuring that the permission is temporary.
Benefits of Implementing a Re-Authentication Policy:
- Increased Security
By requiring additional verification for critical actions or pages, eCatalog ensures that only genuine, authorized actions are executed, reducing the risk of unauthorized access. - Mitigation of Unauthorized Activities
This policy acts as an effective deterrent against unauthorized users attempting to exploit an active session, as they would need to authenticate themselves to proceed. - User Accountability:
Re-authentication enhances accountability by ensuring that users consciously confirm their identity for important actions, aligning with best practices in data security.
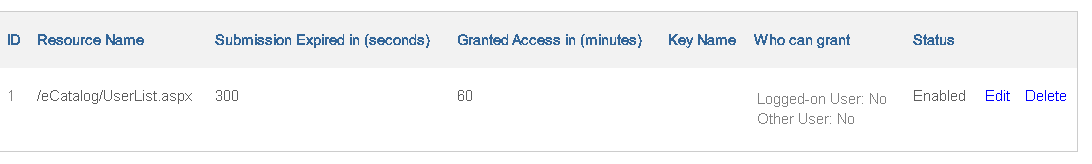
In above example, the User List page is protected. When user trying to access the page, it will prompt the login.
Upon successful re-authentication, user will be granted access for 60 minutes.