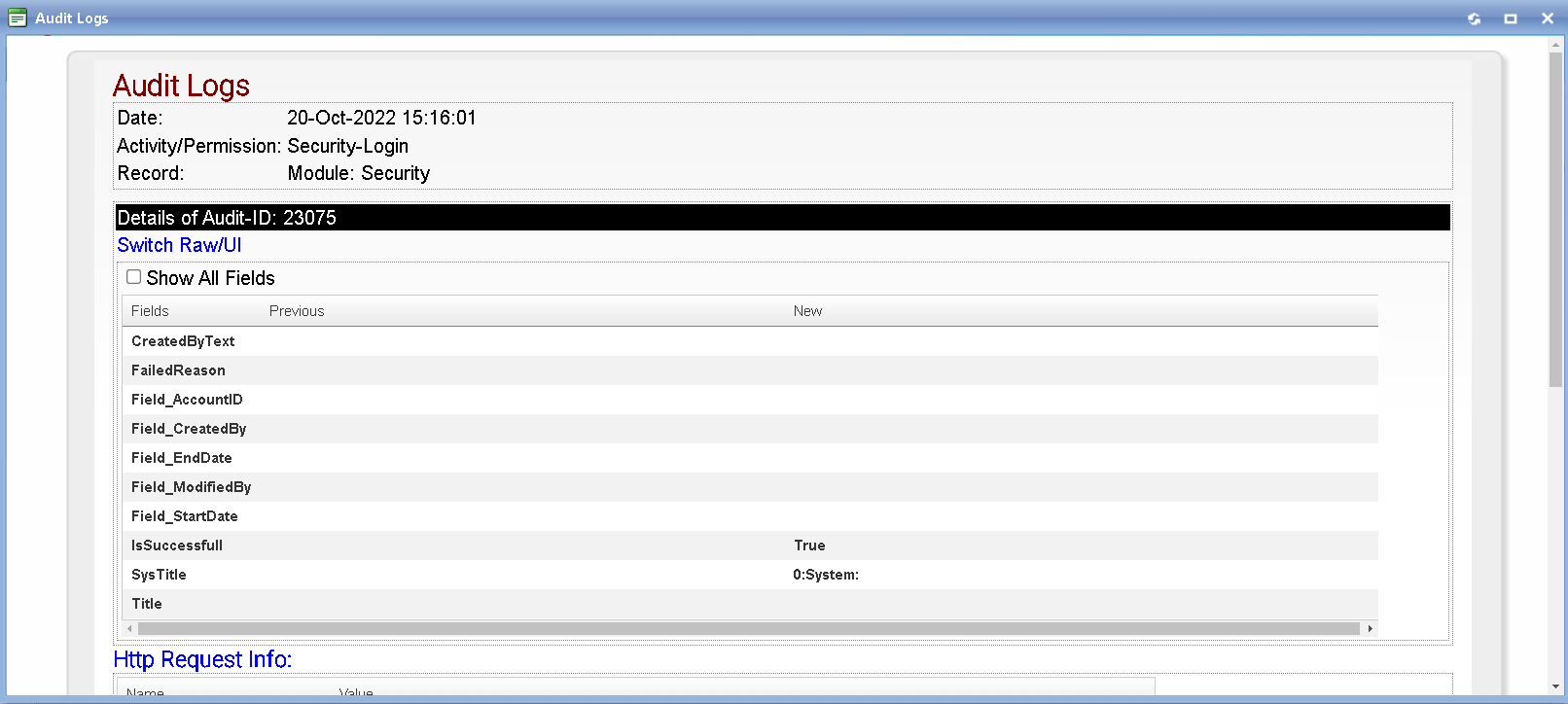
Audit Logs (User Activities Logs)
Detailed Audit Logs and User Activity Tracking in eCatalog
Comprehensive Monitoring for Enhanced Security and Accountability:
eCatalog maintains a rigorous audit log system that records detailed logs of user activities to ensure transparency, security, and compliance within your organization. This system captures every significant action performed, providing administrators with a powerful tool for monitoring and analysis.
Key Activities Logged:
- User Authentication
Logs every instance of user login and logout, helping to track user access patterns and identify unauthorized access attempts. - CRUD Operations
Every create, read, update, and delete action on records is meticulously logged, offering a clear trace of data manipulation and access throughout the system. - Customized Activities
In addition to standard logs, eCatalog can record customized activities specific to different modules. This feature allows for the extension of logging capabilities to meet specialized needs of various operational aspects.
Benefits of Audit Logs/User Activities Logs:
- Enhanced Security
By logging all critical actions, eCatalog helps prevent and detect security breaches by providing timely data on suspicious activities. - Operational Transparency
Audit logs provide an immutable record of all transactions and changes, fostering transparency and trust among users and stakeholders. - Compliance and Reporting
These logs are invaluable for compliance with legal and regulatory requirements, facilitating easy reporting and auditing of user actions and system integrity. - Troubleshooting and Forensics
Detailed logs enable quick diagnosis of operational issues and effective forensic analysis in the event of security incidents or system failures.
Accessing and Managing Audit Logs:
Audit logs can be accessed through the eCatalog’s administrative dashboard. Administrators can search, filter, and review logs based on various criteria such as date, user, and type of activity to easily find specific events or patterns. This accessibility is crucial for timely and effective management of security and operational policies.
Following are information being logged:
- Before Changes data
- After Changes data
- User Name, the person who did the transaction
- Transaction/Activity Name, such as login, add, edit, etc
- Activity Date
- User IP-address
- HTTP_X_FORWARDED_FOR
- Technical information:
- AUTH_USER
- HTTP_ACCEPT
- HTTP_ACCEPT_LANGUAGE
- HTTP_REFERER
- HTTP_USER_AGENT
- HTTPS
- HTTPS_KEYSIZE
- HTTPS_SECRETKEYSIZE
- HTTPS_SERVER_SUBJECT
- LOCAL_ADDR
- LOGON_USER
- QUERY_STRING
- REMOTE_ADDR
- REMOTE_USER
- REQUEST_METHOD
- SCRIPT_NAME
(To view the full image, right-click on the image and select 'Open image in new tab'.)